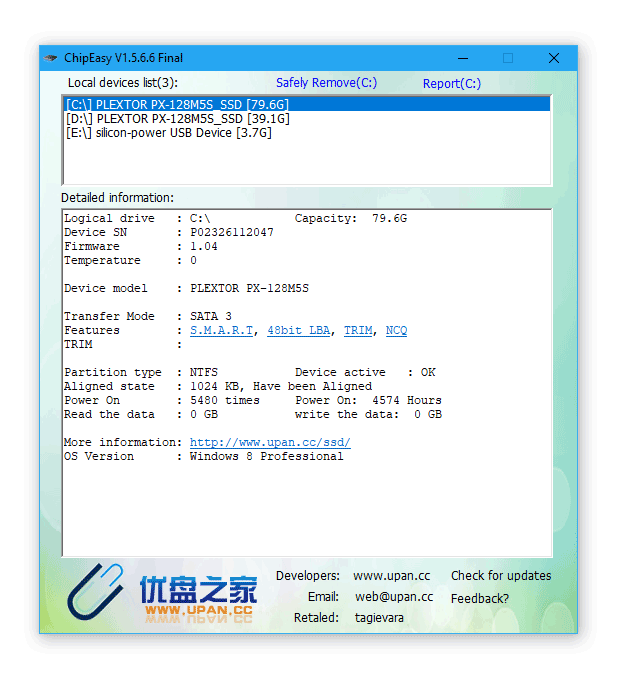
Download Alcor MP Format Tool for repairing corrupted Alcor Chip Controllers.Alcor MP Format Tool allow you to format Alcor AU63xx,AU69xx,AU93xx.Try it now flashdrive-repair.com Flash Drive Repair: Alcor AU63xx,AU69xx,AU93xx USB recovery tool. Download Alcor MP UFD V9.05 format tool for repairing Alcor AU698X and AU3150X chip controllers. Alcor MP UFD V9.05 utility is designed to format corrupted Alcor USB flash drives. Alcor MP UFD V9.05 format tool can update firmware of the following Alcor controllers AU6981, AU6982, AU6983, AU6984, AU6986, AU7640, AU3150B51. Download alcormp v14 to repair corrupted alcor chip controller. Download all bootice tool versions. Alcor usb recovery tool. How to partition a usb flash drive into two windows recognised drives - youtube. Flash drive download alcormp v14 to repair corrupted alcor chip controller. Download the best flash drive tool chip genius 2014 software. In the first step of each data recovery procedure is necessary to determine page layout. Every controller has its unique page structure, in the case of Alcor Micro, it presents as follows. Data area in the majority cases with AU controllers is 1024 Bytes, we can spot as well 512 Byte data area which commonly occurs in low capacity devices. Alcor Micro Corp., mainly provides portable flash memory series control chip and solid state hard disk control chip. Accurately grasp the market trend, adhere to the spirit of professional products and exquisite services, and have excellent performance in product creative design or functional integration, providing innovative, highly integrated and cost-effective products to the world's major.
Blue MicroUSB Flash Drive turns your existing flash drive into a key. Blue Micro USB Flash Drive turns your existing pendrive or flash drive into a key to logon to your pc. This makes it easier for users to manage their computer account passwords.
- BMS_Flash_Logon.zip
- Blue Micro Solutions
- Freeware (Free)
- 532 Kb
- Windows2000,WinXP
MicroUSB flash drive recovery utility restores missing or misplaced files folders from pen drive data storage media. Pen drive recovery support has capability to repair inaccessible documents, text files, pictures, photos, images and photographs etc. ...
- MicronUSBDriveDemo.exe
- Website Monitoring
- Shareware ($38.00)
- 575 Kb
- Win98, WinME, WinNT 3.x, WinNT 4.x, Windows2000, WinXP, Windows2003, Windows Vista
Removable hard disk multimedia file recovery software retrieves all eliminated file folder from any type of devices like memory card, USB card, and external hard drive. Tool can restore virus infected jpeg, png, bmp pictures, images, word document.
- removal-media-data-recovery-demo.exe
- Keylogger
- Shareware ($45.00)
- 703 Kb
- Win98, WinME, WinNT 3.x, WinNT 4.x, Windows2000, WinXP, Windows2003, Windows Vista
Unformat USBpendrive formatted data file folder subfolder retrieval softwarerecover undetected inaccessible documents excel word power point restore lost image photo JPEG MPEG BMP GIF formats tool repair corrupted damaged memory stick key drives. ...
- pen-drive-data-recovery-demo.exe
- Drive Recovery Software
- Shareware ($69.00)
- 598 Kb
- Win98, WinME, WinNT 3.x, WinNT 4.x, Windows2000, WinXP, Windows2003
USBpendrive files salvage tool retrieves all files folders erased due to virus attack, power failure or human error etc. Thumb drive data recovery utility restores deleted or missed images, pictures, movie clips, songs from formatted flash drive.
- pen-drive-data-recovery-demo.exe
- Hard Disk Data Recovery
- Shareware ($45.00)
- 643 Kb
- Win98, WinME, WinNT 3.x, WinNT 4.x, Windows2000, WinXP, Windows2003, Windows Vista
Flash memory files retrieval utility recovers corruptedUSBdrive, pen drive, smart media drive, multimedia drive data, Microsoft office documents, business presentations, audio songs, video albums, images and digital photographs.
- removal-media-data-recovery-demo.exe
- Disk Recovery Tools
- Shareware ($45.00)
- 652 Kb
- Win98, WinME, WinNT 3.x, WinNT 4.x, Windows2000, WinXP, Windows2003, Windows Vista
The multi award winning SilentNight Micro CD Burner is a small standalone multimedia burner without need of any dll files or aspi layer to operate. You can even run it from a USB-Key. If you need to backup or burn some data/movies etc. or would like. ...
- SilentNight Micro CDBurner
- SilentNight Network andSecurity Tools
- Shareware ($29.00)
- Win95, Win98, WinME, WinNT 3.x, WinNT 4.x, Windows2000, WinXP, Windows2003
This is an open-hardware Infrared Remote Controlled USB keyboard, without keys, implemented using a PIC micro-controller and MikroC. IRK! enables you to use your LEARNING remote control to control any system that you can plug a USB keyboard into.
- IRK!-2.03.zip
- instructables
- Freeware (Free)
- 278 Kb
- N/A
The aim of this project is to provide musicians and hobbyists a way of develop its own USB Custom MIDI Controller based on AVR micro-controllers without native USB support.
- AVR-USB-CMC
- sinosoidal
- Freeware (Free)
- Windows
Remora USB File Guard is designed to do file encryption and compression in your USB storage devices. With Remora USB File Guard, you can secure all your files and store them in USB disk anytime and anywhere. And it is totally free.
- remorausbguard_green.exe
- Essential Skill ConsultantsLimited
- Freeware (Free)
- 2.06 Mb
- Win98, WinME, Windows2000, WinXP, Windows2003
Remora USB File Guard Pro is designed to encrypt/compress/auto backup in your USB storage devices. With Remora USB File Guard Pro, you can secure all your files and store them in USB disk anytime and anywhere. And it is portable.
- remorausbguardpro_green.exe
- Essential Skill ConsultantsLimited
- Shareware ($19.95)
- 2.32 Mb
- Win98, WinME, Windows2000, WinXP, Windows2003
Remora USB Disk Guard Pro is a project based file encryption/compression tool, or a strong file encryption/compression switch which can startup from your USB storage devices.
- remorausbdiskguardpro_green.exe
- Essential Skill ConsultantsLimited
- Shareware ($29.95)
- 3.04 Mb
- Win98, WinME, Windows2000, WinXP, Windows2003
 Related:Alcor Micro Usb - Alcor Micro Usb Flash - Alcor Micro Usb Camera - Alcor Micro Usb Drive - Alcor Micro Usb Serial
Related:Alcor Micro Usb - Alcor Micro Usb Flash - Alcor Micro Usb Camera - Alcor Micro Usb Drive - Alcor Micro Usb SerialIdentity Credential & Access Management
As Information Technology (IT) continues to increase in complexity, many organizations struggle with the management of identities and associated access along with with an overabundance of application-specific user accounts and access controls. This problem is further complicated by today’s mix of cloud applications, legacy applications, mobile workforce and the need to access critical information anywhere, and anytime.
External threats such as malware, phishing, and social engineering create an environment where proper selection of Identity and Access Management solutions is critical. Organizations are now working to establish unified, robust, and enterprise-wide user authorization and authentication frameworks to enable streamlined access without compromising the security that more sensitive applications and data demand.
Alcor helps our customers deploy Identity and Access Management solutions that result in significant secure, operational and business process improvement. Our full lifecycle Identity, Credential and Access Management (ICAM) practice is focused on solving difficult enterprise issues associated with user registration, credentialing, authentication, and authorization to physical and logical assets. Our services include:
• Strategic Planning and Program Management: Effective ICAM solutions demonstrate a balance between usability and security. We leverage our full lifecycle understanding of ICAM to support a collaborative benchmarking process that provides our clients with insight into numerous other organizations that share similar challenges. Our subject matter experts bring extensive experience with federal ICAM policy, guidelines, and technical standards. We have conducted in-depth analyses of these standards to support client efforts to develop compliant, cutting edge solutions that maximize user adoption. This includes:
• ICAM Policy Analysis and Development.
• ICAM Technology and Implementation Analysis.
• ICAM Strategy and Implementation Roadmap.
• ICAM Governance and Oversight.
• Program Management.
• System Architecture, Design, and Integration—Vital components of the design process are a practical concept of operations and realistic cost model to enable program decision makers to understand the core functional elements and forecast anticipated costs of the program. This includes:
• Concept of Operations (ConOps).
• Operational Lifecycle Cost Model.
• ICAM / Federated Identity Architecture.
• Registration and Credentialing Workflow Development.
• System component design and integration.
• Process and Application Enablement—Enabling process and applications for ICAM services requires that stakeholders define the business need, identify critical requirements, and develop comprehensive use case scenarios for “as-is” and “to-be” processes. Our team’s comprehensive understanding of the technologies that enable these services ensures that our customers achieve their goals for increased efficiency and productivity. This includes:
• PIV-Enabled Network Logon.
• Single Sign-On (SSO).
• Digital Signature, Encryption and Timestamp.
• E-Authentication.
Risk Management and Compliance
Alcor’s Risk Management and Compliance services addresses the essential elements of cybersecurity, from strategy, governance, and enterprise risk management to security controls, architecture, implementation, and management.
Cybersecurity Risk Quantification:
• Enables enterprise risk management through the quantification of your cybersecurity risk or exposure that provides the insight necessary to articulate your cyber risk appetite, make risk-informed investment decisions, and illuminate risk transfer needs and options.
• Leverages strategic and financial company information to model your cyber operating environment and generate a dashboard view of the “Cyber Value-at-Risk” – the probability of breach, average and severe breach costs, and the top cybersecurity weaknesses.
• Based on data collected from an Enterprise-wide Cybersecurity Program Assessment and additional pertinent organizational information, such as enterprise and business unit revenue and business value of significant IT assets from the CISO and CIO point of view.
Security Technical Controls Review:
• Methodical review of your cybersecurity technical controls environment.• Assesses the enterprise cybersecurity architecture and technical controls for:
• How well the controls implement policy.
• How effectively they support the risk appetite.
• How effectively they meet compliance requirements.
• Applies technical tools to evaluate the operational effectiveness of security controls.
• Based on a repeatable and traceable methodology that draws on accepted security technical controls standards such as Center for Internet Security Critical Security Controls, NIST SP 800-53, Health Insurance Portability and Accountability Act (HIPAA), Payment Card Industry Data Security Standard (PCI DSS), and other sector-specific standards.
Incidence Response and Management
Any organization using information technology is a target for data theft, ransomware, denial of service attacks, and other nefarious attacks – no one is immune. For companies holding customer-sensitive information, federally or state-protected information, personal health information, or even trade secret information, developing an effective incident response plan is crucial.
Alcor provides a broad set of Incident Response and Management Services:
• Prepare – Develop the plan, tools and support when an incident occurs.
• Analyze – Identify the type of incident and defining the scope and potential impact.
• Contain – Limit the exposure and expanse of the incident.
• Remove – Eliminate the threats and threat actors responsible for the incident.
• Recover – Restore normal business operations while reducing the likelihood of a repeat cyber incident.
Alcor Recovery Tool Au6989
Business Continuity & Disaster Recovery
Alcor Recovery Tool Au6989sn

An organization reputation is built on the business continuity, Alcor ensures its clients business continuity with the plan of the action during a business disaster, this involves in creating policies and plans that ensure necessary business functions during a disaster by providing business impact analysis, change management and reporting potential issues. Disaster recovery involves in restore important systems this also involves in reducing business downtime.
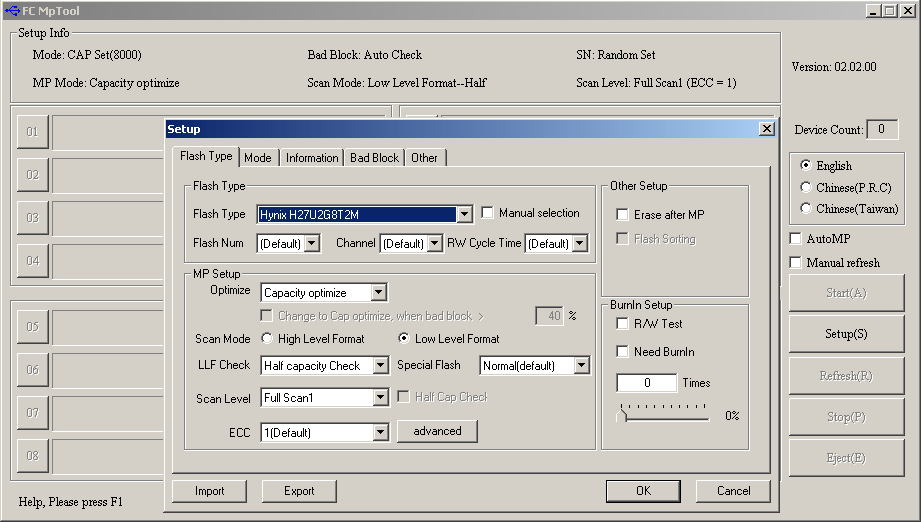
Alcor Recovery Tool V 1.0.0.14 Download
SIEM
Security Information and Event Management (SIEM) is an important piece of any organization’s security strategy. Managed effectively, it can help organizations to protect business operations and intellectual property, meet compliance regulations and enable better detection and faster response to security incidents.
Demand for SIEM technology is high, but that doesn’t mean that every business has deployed a SIEM solution or that all existing implementations are running smoothly.
Alcor utilizes its SIEM expertise to provide you with services at all stages of implementation, from product selection and testing, to implementation, tuning, and functional testing.
Vulnerability Scanning
Alcor performs vulnerability scanning using industry standard assessment tools as well as manual attack techniques meant to uncover weaknesses that are often missed with automated vulnerability scanning alone. In addition to reporting on the vulnerabilities we discover, Alcor provides remediation guidance and risk scoring to ensure your teams have the information necessary to prioritize remediation efforts.